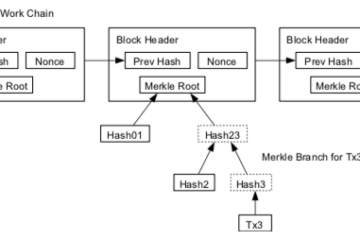
Bitcoin’s proof-of-work mechanism, as many of you will know, requires the fast and repetitive re-computation of a hash value based on the current block candidate. This is the job of the miners, they build a block candidate, inject a random number to add some variation, then compute a hash. If the hash is below the current difficulty level – a universally known value which provides a numerical upper acceptable limit on valid hashes – then they get to add a new block. If the hash value exceeds the difficulty then they must try again with a new random number. The difficulty parameter is dynamically adjusted to regulate finding a valid result only once every 10 minutes, globally.
What is less well known is that success in this process is called a partial pre-image crack. That’s right, ‘crack’!
A quick digression to check we all know the difference between crack and hack:
- Crack: Think safe cracking but in 1978, by a 15 year old, to an IBM office network, which cost $10m to install and protects a list of 99 client’s fax numbers.

- Hack: Think hackathons, or hacking away at something to make it better and better despite the diminishing returns, just because you are satisfied with nothing less than perfection.

Hacking became a common term for cracking at some point, misconstrued by the mass media. Bitcoin’s blockchain is hacked away at continually by miners, making its older blocks more and more immutable as time passes. Why do they spend their time exerting this effort? Because they seek to bury the ledger’s history under a mountain of new hashes all chained together, in return for a reward paid in freshly minted bitcoins. Bitcoins buy immutability. The more they are worth, the more resources the miners throw at their task, the more immutable the ledger history becomes.
Cryptographically secure hash functions, including Bitcoin’s SHA-256 variant, are designed to be pre-image resistant. This means that it should be computationally infeasible to find an input (aka a pre-image, aka a Bitcoin block) which satisfies an already known hash value (aka the image). Ideally it would be simply impossible to find a pre-image for a known hash, but in the practical world, there is always a chance that a random guess will produce the right pre-image, therefore we only ask good hashing algorithms to be pre-image resistant up to the degree of ‘computational infeasibility’.
Bitcoin exploits this weakness in SHA-256 and turns in to a strength. If the rules of the game are that miners must competitively throw computation power at finding a pre-image (ie, cracking the hash) then collectively they are going to massively outpace anyone who actually wants to pre-image attack Bitcoin for devious purposes – everyone is already attacking it constantly. Bitcoin blends the terms hacking and cracking into a single activity.
For the sake of completeness, note that the miners find partial cracks, not full ones. If the current mining difficulty parameter requires a block hash to have 17 leading zeros, then that is the numerical threshold under which any hash will be considered a successful ‘partial crack’. If the difficulty was at it’s theoretical maximum hardness of 0 (zero) then there would be such a small set of valid pre-images (aka ‘pre-image collisions’) which would satisfy a hash of ‘0’, the miners would never find a result. SHA-256 isn’t a perfect algorithm, but it is still a very tough nut to crack. The difficulty parameter is in fact the opposite of what it’s called, it’s there to make life easier for miners, it’s there to make the pre-image crack artificially easier than it naturally would be, to the tune of about 10 minutes of collective number crunching.
Within this game we have the market value of bitcoin acting as an immutability bell weather. If people demand bitcoin, the price goes up, mining increases, the task of finding a valid pre-image becomes harder, and the harder it is for anyone else to rearrange the ledger and then come up with a competing partial pre-image crack to validate their accounting fraud.
The network depends on the currency, and the currency depends on the network. This is an elegant example of a network economy and most, if not all other decentralised systems, have comparable but often less visible dynamics at play.